Cryptography, a scientific field that has existed even before the beginning of computer science. This article looks at the development symmetric crypto-system, which falls within the framework of image security, by Advanced Encryption Standard (AES- Advanced Encryption Standard) algorithms. AES algorithm is not integrity protected. Cryptanalysis could use modified encrypted image of each ciphered bloc for generating oracle and getting the key. A new crypto-system uses hash function named AES-GCM (Advanced Encryption Standard-) for solving this problem. Using Galois Counter Mode (GCM) combined with Secure Hash Algorithm 256 bits (SHA-256) or BLAKE2s hash function, the old mode of ciphering like: Cipher FeedBack (CFB), Output FeedBack (OFB), Cipher Block Chaining (CBC), Electronic Codebook Block (ECB) and CounTeR (CTR) mode encryption, will increase the security level at confidentiality and integrity. In this article, robustness of the crypto-system will be evaluated by multiple criteria, indeed the statistical analysis, sensitivity measurement and performance measurement. For the statistical analysis, the histogram is flat and the correlation between adjacent pixel is not linear for the encrypted image. The relation between clear image and encrypted image doesn’t exist. For the sensitivity analysis, Number of Pixel Changing Rate (NPCR) and Unified Averaged Changed Intensity (UACI) permit to avoid differential attack of the crypto-system. The two values are respectively near 99% and 30%. For performance measurement, the similarity of the decrypted image and original image will be tested. The Peak Signal to Noise Ratio (PSNR) and Mean Square Error (MSE) are equals of infinity and zero. The decrypted image and original image are the same. The integrity of the image on the crypto-system will be evaluated by modifying one bit of the encrypted image. The decryption process doesn’t give decrypted image and show that the tag value is incorrect.
| Published in | Applied Engineering (Volume 8, Issue 1) |
| DOI | 10.11648/j.ae.20240801.12 |
| Page(s) | 14-30 |
| Creative Commons |
This is an Open Access article, distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution and reproduction in any medium or format, provided the original work is properly cited. |
| Copyright |
Copyright © The Author(s), 2024. Published by Science Publishing Group |
AES, Cryptography, GCM, Hash, Security, Symmetric
key size | Possible combination |
|---|---|
1 bit | 2 |
2 bits | 4 |
4 bits | 16 |
8 bits | 256 |
16 bits | 65536 |
32 bits | 4.2×10 9 |
56 bits (DES) | 7.2×10 16 |
64 bits | 1.8×10 19 |
128 bits (AES) | 3.4×10 38 |
192 bits (AES) | 6.2×10 57 |
256 bits (AES) | 1.1×10 77 |
Uses case | crypto system |
|---|---|
Use case 1 | User must insert file to encrypt or decrypt. |
Use case 2 | The user must enter the password for authentication. |
Use case 3 | The user must choose a hash function (SHA-256, BLAKE2s). |
Use case 4 | The user must choose the AES mode (GCM, CFB, OFB, CBC, ECB, CTR). |
Use case 5 | The user must choose between encrypting or decrypting. |
Pictures | Histograms | |
|---|---|---|
original | ||
GCM | ||
CFB | ||
OFB | ||
CBC | ||
ECB | ||
CTR |
Pictures | Histograms | |
|---|---|---|
original | ||
GCM | ||
CFB | ||
OFB | ||
CBC | ||
ECB | ||
CTR |
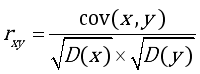 (5)
(5) 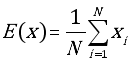 (6)
(6) 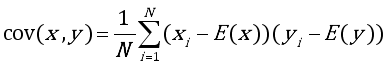 (7)
(7) 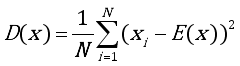 (8)
(8) Correlation (horizontal, vertical, diagonal) | |
|---|---|
Original | |
GCM | |
CFB | |
OFB | |
CBC | |
ECB | |
CTR |
Correlation (horizontal, vertical, diagonal) | |
|---|---|
original | |
GCM | |
CFB | |
OFB | |
CBC | |
ECB | |
CTR |
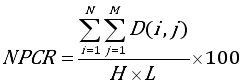 (9)
(9) SHA | BLAKE | |
|---|---|---|
GCM | 99.61004586260732 | 99.6089480874317 |
CFB | 99.61553473848556 | 99.60467896174863 |
OFB | 99.60431303669009 | 99.6135831381733 |
CBC | 99.6173643637783 | 99.60260538641687 |
ECB | 99.62163348946136 | 99.61529078844653 |
CTR | 99.6044350117096 | 99.61346116315377 |
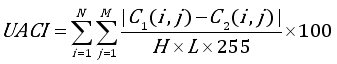 (11)
(11) SHA | BLAKE | |
|---|---|---|
GCM | 30.415273281456106 | 30.485258242653657 |
CFB | 30.46358112918564 | 30.487924473080636 |
OFB | 30.44087368555215 | 30.486615752871348 |
CBC | 30.432582254226148 | 30.454480357729125 |
ECB | 30.3907606075344 | 30.419510837134716 |
CTR | 30.418087316906693 | 30.41796390688642 |
Hash | SHA-256 | BLAKE2S | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Modes | GCM | CFB | OFB | CBC | ECB | CTR | GCM | CFB | OFB | CBC | ECB | CTR |
MSE | 0 | 0 | ||||||||||
Hash | SHA-256 | BLAKE2S | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Modes | GCM | CFB | OFB | CBC | ECB | CTR | GCM | CFB | OFB | CBC | ECB | CTR |
PSNR | Infinity | Infinity | ||||||||||
SHA | BLAKE | |
|---|---|---|
GCM | 7.63747834 | 7.63830899 |
CFB | 7.63881666 | 7.63738745 |
OFB | 7.63907246 | 7.64134985 |
CBC | 7.63743805 | 7.64047588 |
ECB | 7.63787775 | 7.63747895 |
CTR | 7.63872385 | 7.6368872 |
Original image | Encrypted | Tag in hexadecimal |
|---|---|---|
(Non-Modified) | 390f6927 bd6780d3 09ccbb19 a15265a1 | |
(Modified) | Tag Incorrect | |
(Non-modified) | b289b331 343ef8b6 70940578 a3a26b3c | |
(Modified) | Tag Incorrect | |
(Non-modified) | 9552de48 642ecc75 bc64e29e c526ae8a | |
Modified | Tag Incorrect |
| [1] | Flevina Jonese D'souza and Dakshata Panchal, (2017). Advanced encryption standard (AES) security enhancement using hybrid approach, in IEEE International Conference on Computing, Communication and Automation (ICCCA), 21 December 2017, Greater Noida, India, |
| [2] | Megha Chakole and S. S. Dorle (2023). Design of Advanced Encryption Standard Algorithm, in IEEE International Conference On Computing, Communication, Control And Automation (ICCUBEA), 16 January 2023, Pune, India, |
| [3] | Simon Heron (2009). Advanced Encryption Standard (AES), in Network Security, Volume 2009, Issue 12, December 2009, pp. 8-12, |
| [4] | Yan Qing. Zhong, Jian Ming. Wang, Z. F. Zhao, D. Y. Yu and L. Li (2007). A Low-cost and High Efficiency Architecture of AES Crypto-engine, in IEEE International Conference on Communications and Networking in China, 07 March 2008, Shanghai, China, |
| [5] | Salim M. Wadia, b and Nasharuddin Zainala, (2013). Rapid Encryption Method Based on AES Algorithm for Grey Scale HD Image Encryption, in Procedia Technology, Iraq, 2013, pp. 51–56, |
| [6] | Venkata Krishna Pavan Kalubandi, Hemanth Vaddi, Vishnu Ramineni and Agilandeeswari Loganathan, (2017). A novel image encryption algorithm using AES and visual cryptography, in IEEE International Conference on Next Generation Computing Technologies (NGCT), 16 March 2017, Dehradun, India, |
| [7] | Amandeep Singh, Praveen Agarwal and Mehar Chand, (2019), Image Encryption and Analysis using Dynamic AES, in IEEE International Conference on Optimization and Applications (ICOA), 03 june 2019, Kenitra, Morocco, |
| [8] | Ijaz Khalid, Tariq Shah, Sayed M. Eldin, Dawood Shah, Muhammad Asif and Imran Saddique (2022). An Integrated Image Encryption Scheme Based on Elliptic Curve, in IEEE Access, vol. 11, 16 December 2022, pp. 5483–5501, |
| [9] | Miguel León Chávez, Francisco Rodríguez Henríquez and Emmanuel López Trej (2007). AES-CCM Implementations for the IEEE 802.15.4 Devices, in IFAC Proceedings, vol. 40, issue 22, 2007, pp. 223-229, |
| [10] |
Arshad Aziz and Nassar Ikram (2007). An FPGA-based AES-CCM Crypto core for IEEE 802.11i architecture, in International Journal of Network Security, vol. 5, issue 2, September 2007, pp. 224–232,
http://ijns.jalaxy.com.tw/contents/ijns-v5-n2/ijns-2007-v5-n2-p224-232.pdf |
| [11] | Rei Ueno, Sumio Morioka, Naofumi Homma and Takafumi Aoki, (2016). A High Throughput/Gate AES Hardware Architecture by Compressing Encryption and Decryption Datapaths - Toward Efficient CBC-Mode Implementation, |
| [12] | Suhyeon Jeon and Jihwan P. Choi (2019). CFB-AES-TURBO: Joint Encryption and Channel Coding for Secure Satellite Data Transmission, in IEEE International Conference on Communications (ICC), 15 July 2019, Shanghai, China, |
| [13] | Suhyeon Jeon, Jeongho Kwak, Jihwan and P. Choi (2022), Cross-Layer Encryption of CFB-AES-TURBO for Advanced Satellite Data Transmission Security, in IEEE Transactions on Aerospace and Electronic Systems, vol. 58, issue. 3, June 2022, pp. 2192 – 2205, |
| [14] | Mahmoud Alfadel, El-Sayed M. El-Alfy and Khaleque Md Aashiq Kamal (2017). Evaluating time and throughput at different modes of operation in AES algorithm, in International Conference on Information Technology (ICIT), 23 octobre 2017, Amman, Jordan, |
| [15] | Mohamed Boussif (2022). On The Security of Advanced Encryption Standard (AES), in IEEE International Conference on Engineering, Applied Sciences, and Technology (ICEAST), 20 July 2022, Chiang Mai, Thailand, |
| [16] | Razvi Doomun, Jayramsingh Doma and Sundeep Tengur (2008), AES-CBC software execution optimization, in IEEE International Symposium on Information Technology, 26 September 2008, Kuala Lumpur, Malaysia, |
| [17] | Shashank Srivastava, Avinash Kumar Singh and G. C. Nandi (2012). Inter Cipher Block Diffusion: A Novel Transformation for Proposed Parallel AES, in Procedia Technology vol. 6, 2012, pp 872-879, |
| [18] | Tomoya Hikida, Yasuyuki Nogami, Md Arshad Ali and Yuta Kodera (2022), Comparison of conversion matrices for a compact AES-CTR defined over an isomorphic field, in IEEE International Technical Conference on Circuits/Systems, Computers and Communications (ITC-CSCC), 03 October 2022, |
| [19] | Tom St Denis and Simon Johnson (2007). Advanced Encryption Standard, in Cryptography for Developers, 2007. |
| [20] | Youngbeom Kim and Seog Chung Seo (2021), Efficient Implementation of AES and CTR_DRBG on 8-Bit AVR-Based Sensor Nodes, in IEEE Access vol. 9, 16 February 2021, pp. 30496 – 30510, |
| [21] | Ignacio Algredo-Badillo, Claudia Feregrino-Uribe, René Cumplido and Miguel Morales-Sandoval (2010), Efficient hardware architecture for the AES-CCM protocol of the IEEE 802.11i standard, in Computers & Electrical Engineering vol. 36, issue 3, May 2010, pp. 565-577, |
| [22] | Benjamin Buhro, Karl Fritz, Barry Gilbert and Erik Daniel (2016). A highly parallel AES-GCM core for authenticated encryption of 400 Gb/s network protocols, in IEEE International Conference on ReConFigurable Computing and FPGAs (ReConFig), 01 February 2016, Riviera Maya, Mexico, |
| [23] | Byung-Yoon Sung; Ki-Bbeum Kim; Kyung-Wook Shin (2018). An AES-GCM authenticated encryption crypto-core for IoT security, in IEEE International Conference on Electronics, Information, and Communication (ICEIC), 05 April 2018, Honolulu, HI, USA, |
| [24] | Eduardo Mobilon and Dalton Soares Arantes (2021). 100 Gbit/s AES-GCM Cryptography Engine for Optical Transport Network Systems: Architecture, Design and 40 nm Silicon Prototyping, in Microelectronics Journal vol. 116, October 2021, |
| [25] | Nabihah Ahmad, Lim Mei Wei, and M. Hairol Jabbar (2017), Advanced Encryption Standard with Galois Counter Mode using Field Programmable Gate Array, in International Conference on Green and Sustainable Computing (ICoGeS), 2017, |
| [26] |
Jack Zhao, Performance analysis of cryptographic functions on programmable NICS, in Dalhousie University, August 2022, Halifax, Nova Scotia,
https://dalspace.library.dal.ca/bitstream/handle/10222/81823/JackZhao2022.pdf |
| [27] |
Sitraka Rakotondramanana,
https://github.com/SitrakaResearchAndPOC/aes_bloc_ciphering_modes |
| [28] | Hatice Koç, Ali Mert Erdoğan, Yousef Barjakly and Serhat Peker, UML Diagrams in Software Engineering Research: A Systematic Literature Review, in MDPI International Management Information Systems Conference, 10 March 2021, |
| [29] | Mert Ozkaya and Ferhat Erata, A survey on the practical use of UML for different software architecture viewpoints, in Elsevier Information and Software Technology Volume 121, May 2020, 106275, |
| [30] | Mohammad N. Alanazi, Basic Rules to Build Correct UML Diagrams, in IEEE International Conference on New Trends in Information and Service Science, 25 September 2009, Beijing, China, |
APA Style
Sitraka, R. R., Malalatiana, R. H. (2024). Evaluations of Crypto-System AES Using Multiple Bloc Ciphering Mode. Applied Engineering, 8(1), 14-30. https://doi.org/10.11648/j.ae.20240801.12
ACS Style
Sitraka, R. R.; Malalatiana, R. H. Evaluations of Crypto-System AES Using Multiple Bloc Ciphering Mode. Appl. Eng. 2024, 8(1), 14-30. doi: 10.11648/j.ae.20240801.12
@article{10.11648/j.ae.20240801.12,
author = {Rakotondramanana Radiarisainana Sitraka and Ramafiarisona Hajasoa Malalatiana},
title = {Evaluations of Crypto-System AES Using Multiple Bloc Ciphering Mode
},
journal = {Applied Engineering},
volume = {8},
number = {1},
pages = {14-30},
doi = {10.11648/j.ae.20240801.12},
url = {https://doi.org/10.11648/j.ae.20240801.12},
eprint = {https://article.sciencepublishinggroup.com/pdf/10.11648.j.ae.20240801.12},
abstract = {Cryptography, a scientific field that has existed even before the beginning of computer science. This article looks at the development symmetric crypto-system, which falls within the framework of image security, by Advanced Encryption Standard (AES- Advanced Encryption Standard) algorithms. AES algorithm is not integrity protected. Cryptanalysis could use modified encrypted image of each ciphered bloc for generating oracle and getting the key. A new crypto-system uses hash function named AES-GCM (Advanced Encryption Standard-) for solving this problem. Using Galois Counter Mode (GCM) combined with Secure Hash Algorithm 256 bits (SHA-256) or BLAKE2s hash function, the old mode of ciphering like: Cipher FeedBack (CFB), Output FeedBack (OFB), Cipher Block Chaining (CBC), Electronic Codebook Block (ECB) and CounTeR (CTR) mode encryption, will increase the security level at confidentiality and integrity. In this article, robustness of the crypto-system will be evaluated by multiple criteria, indeed the statistical analysis, sensitivity measurement and performance measurement. For the statistical analysis, the histogram is flat and the correlation between adjacent pixel is not linear for the encrypted image. The relation between clear image and encrypted image doesn’t exist. For the sensitivity analysis, Number of Pixel Changing Rate (NPCR) and Unified Averaged Changed Intensity (UACI) permit to avoid differential attack of the crypto-system. The two values are respectively near 99% and 30%. For performance measurement, the similarity of the decrypted image and original image will be tested. The Peak Signal to Noise Ratio (PSNR) and Mean Square Error (MSE) are equals of infinity and zero. The decrypted image and original image are the same. The integrity of the image on the crypto-system will be evaluated by modifying one bit of the encrypted image. The decryption process doesn’t give decrypted image and show that the tag value is incorrect.
},
year = {2024}
}
TY - JOUR T1 - Evaluations of Crypto-System AES Using Multiple Bloc Ciphering Mode AU - Rakotondramanana Radiarisainana Sitraka AU - Ramafiarisona Hajasoa Malalatiana Y1 - 2024/04/02 PY - 2024 N1 - https://doi.org/10.11648/j.ae.20240801.12 DO - 10.11648/j.ae.20240801.12 T2 - Applied Engineering JF - Applied Engineering JO - Applied Engineering SP - 14 EP - 30 PB - Science Publishing Group SN - 2994-7456 UR - https://doi.org/10.11648/j.ae.20240801.12 AB - Cryptography, a scientific field that has existed even before the beginning of computer science. This article looks at the development symmetric crypto-system, which falls within the framework of image security, by Advanced Encryption Standard (AES- Advanced Encryption Standard) algorithms. AES algorithm is not integrity protected. Cryptanalysis could use modified encrypted image of each ciphered bloc for generating oracle and getting the key. A new crypto-system uses hash function named AES-GCM (Advanced Encryption Standard-) for solving this problem. Using Galois Counter Mode (GCM) combined with Secure Hash Algorithm 256 bits (SHA-256) or BLAKE2s hash function, the old mode of ciphering like: Cipher FeedBack (CFB), Output FeedBack (OFB), Cipher Block Chaining (CBC), Electronic Codebook Block (ECB) and CounTeR (CTR) mode encryption, will increase the security level at confidentiality and integrity. In this article, robustness of the crypto-system will be evaluated by multiple criteria, indeed the statistical analysis, sensitivity measurement and performance measurement. For the statistical analysis, the histogram is flat and the correlation between adjacent pixel is not linear for the encrypted image. The relation between clear image and encrypted image doesn’t exist. For the sensitivity analysis, Number of Pixel Changing Rate (NPCR) and Unified Averaged Changed Intensity (UACI) permit to avoid differential attack of the crypto-system. The two values are respectively near 99% and 30%. For performance measurement, the similarity of the decrypted image and original image will be tested. The Peak Signal to Noise Ratio (PSNR) and Mean Square Error (MSE) are equals of infinity and zero. The decrypted image and original image are the same. The integrity of the image on the crypto-system will be evaluated by modifying one bit of the encrypted image. The decryption process doesn’t give decrypted image and show that the tag value is incorrect. VL - 8 IS - 1 ER -